Practical Istio - Private Kubernetes Deployment

Table of Contents
- Practical Istio - Introduction
- Practical Istio - Private Kubernetes Deployment
- Practical Istio - Init & Install
- Practical Istio - Ingress Gateway
- Practical Istio - Virtual Services
Introduction
In this post we're going to go through the orchestration of the resources needed to test out Istio. To do this nice and cleanly Deployment Manager templates will be used for the various pieces. The results should give us a private kubernetes deployment.
Note: More information about how the deployment manager templates from this repo work can be found in my other post Bootstrap GKE with Deployment Manager on GCP. Check out the original repository: https://github.com/t04glovern/gke-dm-bootstrap.
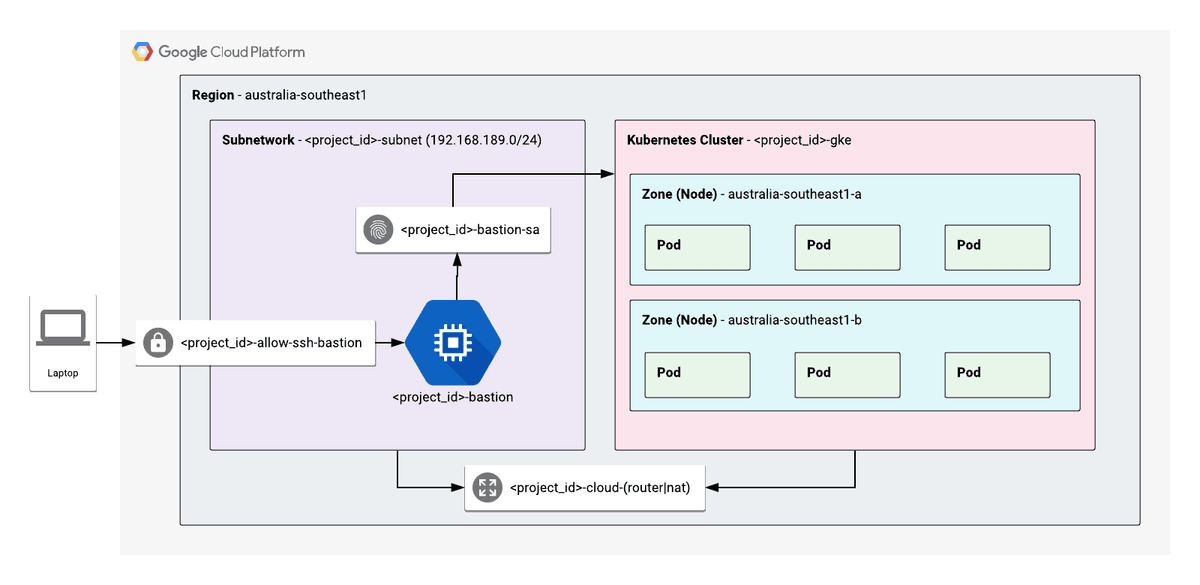
Architecture
Below is the reference architecture for the GKE hosted Kubernetes network.
Deployment
There’s a script within the root directory of the project called deploy.sh that handles most of the resource creation for you given command line parameters.
The general structure is ./deploy.sh $project_id $resource $action where:
- project_id: Project ID retrieved from the previous step (mine was devopstar)
- resource: Lowercase name of the resource we want to deploy. You can find the yaml files referred to within the
resourcesfolder - action: create or delete
An example of deployment of all the recommended infrastructure would be to run the following in order
./deploy.sh devopstar iam create
./deploy.sh devopstar network create
./deploy.sh devopstar cloud-router create
./deploy.sh devopstar gke create
./deploy.sh devopstar bastion createNote: The region for deployment is set to _australia-southeast1_ currently to cut down on variation within the templates and the guide. If you do want to change this you'll need to ensure the rest of the templates have their region changed also.
Manage Cluster
We need to copy all the resources from the repository up to the bastion server. This is because it is the only server that has permission to talk to Kubernetes from within our private network. Run the following command to SCP the k8s directory onto the bastion server.
gcloud compute scp \
--recurse ./k8s* $PROJECT_ID-bastion:~/ \
--zone australia-southeast1-aNext we can connect to the bastion server over SSH by running the following:
gcloud compute ssh $PROJECT_ID-bastion \
--project $PROJECT_ID \
--zone australia-southeast1-aFinally, auth against the GKE instance from the bastion server by running the following:
gcloud container clusters get-credentials $PROJECT_ID-gke \
--project $PROJECT_ID \
--region australia-southeast1Testing
Confirm that you have access to the cluster by running the following command and inspecting the output:
$ kubectl cluster-info
# Kubernetes master is running at https://XXX.XXX.XXX.XXXWhats Next?
In the next section we'll be initialising and installing Istio onto our Kubernetes cluster.